Fiber Network Security: Protect Your Fiber Optic Infrastructure from Cyber Threats
Fiber Network Security: Protect Your Fiber Optic Infrastructure from Cyber Threats
Blog Article
The Vital Role of Data and Network Safety And Security in Shielding Your Details
In an era where information breaches and cyber dangers are increasingly prevalent, the significance of durable data and network protection can not be overemphasized. The execution of effective protection actions, such as security and access controls, is essential to keeping trust and functional honesty.
Understanding Data Security
In today's electronic landscape, a frustrating bulk of organizations face the intricacies of data protection. This crucial component of infotech entails protecting delicate data from unapproved gain access to, corruption, or theft throughout its lifecycle. Information protection incorporates different approaches and modern technologies, consisting of encryption, accessibility controls, and data masking, all focused on safeguarding details versus breaches and vulnerabilities.
A fundamental element of information safety is the recognition and classification of data based upon its sensitivity and importance. This classification helps organizations prioritize their protection initiatives, assigning resources to secure one of the most crucial information properly. In addition, executing durable plans and procedures is necessary to ensure that workers recognize their role in preserving information protection.
Regular audits and evaluations help in recognizing potential weak points within an organization's information safety and security structure. In addition, employee training is vital, as human error remains a considerable variable in data breaches. By cultivating a society of safety recognition, companies can alleviate threats linked with expert risks and negligence.
Significance of Network Protection
Network security stands as a keystone of a company's total cybersecurity technique, with approximately 90% of companies experiencing some type of cyber risk in recent years. The significance of network safety lies in its ability to safeguard sensitive information and preserve the honesty of business procedures. By guarding network frameworks, organizations can stop unauthorized accessibility, data breaches, and various other harmful tasks that might endanger their properties and online reputation.
Implementing robust network protection gauges not just aids in mitigating risks but likewise fosters depend on among stakeholders and customers. When consumers are guaranteed that their individual and monetary details is safe, they are more probable to engage with the organization, leading to improved client commitment and service development.
Additionally, a well-structured network security structure promotes compliance with various regulatory needs. Organizations should abide by industry criteria and legal requireds concerning information protection, and effective network safety practices can ensure conformity, thereby staying clear of potential charges.

Typical Cyber Threats
Organizations need to continue to be cautious versus a selection of cyber threats that can weaken their network safety and security initiatives. Amongst one of the most common hazards is malware, which incorporates viruses, worms, and ransomware that can interrupt procedures, take data, or hold information captive. Phishing strikes, where destructive stars impersonate relied on entities to deceive individuals into exposing sensitive details, remain to expand in refinement, making customer education crucial.
An additional widespread hazard is dispersed denial-of-service (DDoS) attacks, which overload systems with web traffic, rendering them unavailable to genuine users. Expert dangers, whether accidental or willful, posture substantial look at here threats as workers might inadvertently subject sensitive information or deliberately exploit their accessibility for malicious functions.
In addition, vulnerabilities in software application and hardware can be manipulated by cybercriminals, highlighting the significance of normal updates and spot monitoring. Social engineering strategies additionally complicate the landscape, as enemies control individuals right into disclosing confidential info with mental control.
As these risks progress, companies must keep an aggressive technique to recognize, minimize, and react properly to the ever-changing cyber danger landscape, guarding their beneficial info and preserving count on with stakeholders. fft pipeline protection.
Ideal Practices for Defense
Implementing robust safety and security actions is essential for guarding delicate info and maintaining functional stability. Organizations needs to start by performing comprehensive threat assessments to determine susceptabilities within their systems. This positive strategy enables the prioritization of protection efforts customized to the specific demands of the company.
Adopting strong password policies is crucial; passwords ought to be complicated, on a regular basis changed, and managed making use of safe and secure password administration devices. Multi-factor authentication (MFA) adds an additional layer of protection by requiring additional confirmation techniques, hence decreasing the threat of unauthorized gain access to.
Routine software program updates and patch monitoring are critical to safeguard versus recognized vulnerabilities. Applying firewall programs and invasion detection systems can better protect networks from exterior hazards. Worker training is just as essential; personnel anchor must be educated on acknowledging phishing attempts and comprehending the significance of information safety and security protocols.
Information encryption should be used for sensitive info, both at rest and en route, to guarantee that also if data is obstructed, it continues to be inaccessible (fft pipeline protection). Companies have to create and consistently examination event reaction prepares to make certain speedy action in the occasion of a safety and security violation. By sticking to these best methods, organizations can improve their safety position and protect their critical information properties
Future Trends in Safety
The landscape of information and network protection additional hints is continuously developing, driven by developments in modern technology and the boosting sophistication of cyber threats. As organizations significantly adopt cloud computing and IoT tools, the paradigm of protection will change toward a zero-trust design. This technique emphasizes that no entity-- outside or inner-- is naturally trusted, mandating verification at every access factor.
Moreover, making use of artificial intelligence and maker understanding in safety and security procedures is on the increase. These technologies enable predictive analytics, permitting organizations to identify susceptabilities and possible risks prior to they can be made use of. Automation will likely play a critical function in enhancing protection reactions, decreasing the time taken to mitigate violations.
In addition, regulatory structures will remain to tighten, requiring more strict compliance actions. Organizations needs to remain abreast of developing regulations to ensure they fulfill security requirements.
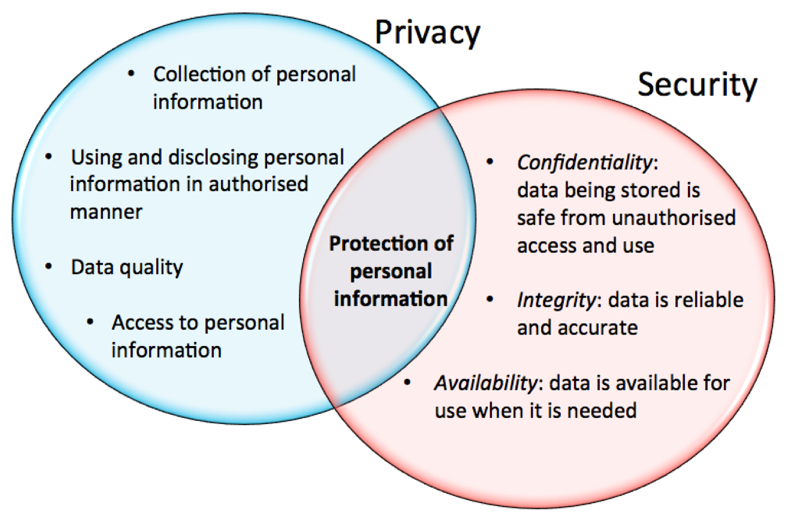
Verdict
In conclusion, the relevance of information and network protection can not be overemphasized in the contemporary electronic landscape. With the frequency of cyber risks and the raising complexity of governing needs, organizations have to embrace extensive protection actions to secure delicate info.
In a period where data violations and cyber hazards are significantly widespread, the value of robust information and network safety can not be overemphasized. Information security incorporates different techniques and modern technologies, consisting of security, gain access to controls, and information masking, all aimed at safeguarding details versus breaches and susceptabilities.
An essential facet of information protection is the identification and category of data based on its sensitivity and significance.The landscape of data and network safety is constantly developing, driven by improvements in technology and the increasing refinement of cyber risks.In verdict, the importance of information and network protection can not be overemphasized in the contemporary digital landscape.
Report this page